Back in March, I wrote a blog about secure laptops based on some work Lynx was doing in this area. I committed to providing some ongoing updates via our website in due course. At the time, this was based some work with a partner that is focused on the Commercial Solutions for Classified (CSfC) program. I hope to be able to share more details in the public domain about this partnership in the not-too-distant future.
In this COVID-19 era, we are seeing several sectors slow down. Higher level autonomous vehicles is one example, with companies like Audi announcing in 2Q20 they are reducing engineering efforts around level 3 autonomy for the A8, preferring instead to focus on level 2 functionality which is seen to be monetizable more quickly. Other sectors like robotics—both in the sky and on the ground—seem to be ramping up, particularly in Asia and North America. Similarly, the inquiries around secure laptops and, increasingly, cloud data center and edge infrastructure, have significantly increased in the past three months. Beyond the types of government organizations that view CSfC functionality as important, a broader range of financial, industrial and healthcare companies are looking to increase the robustness of their devices and network infrastructure.
With work from home set to continue for a long period of time (in some cases like Fujitsu, maybe forever!), CIOs have to rethink their network strategies. Companies would traditionally plan for about 20% of their workers to be remote and 80% in an office environment. That scenario has completely flipped. CIOs want functionality like data encryption and VPN to be permanently enabled. Many companies have taken the approach of completely disabled the insertion of USB devices. Increasingly, this needs to be supported with more fine-grained control than simply enabled/disabled. Instead, this functionality should be allowed or prevented on a per VM basis.
Our demonstration platform harnesses an eight core Intel® Core™ i7 processor, with cores allocated for a secure Windows 10 and an unprotected Windows operating system. There are separate disk partitions for each instance. Applications in the protected OS environment have data flows through a corporate or cloud security service via VPN. The unprotected OS is strictly isolated.
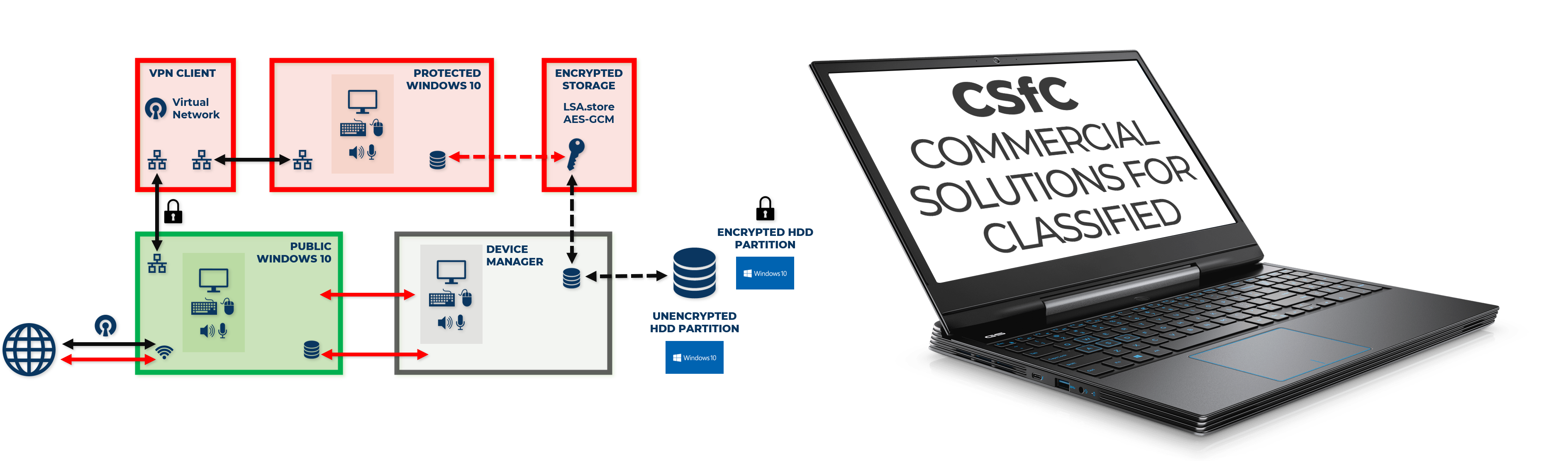
We have recently posted up a page on our website that articulates our thoughts about this use case for our LynxSecure separation kernel. We will be adding to this regularly including a video of the demonstration unit. One of our competitors referenced us in one of their recent press releases which shows we are on their radar screen around multicore certification. They have had a somewhat “surprising” approach of doing this over the years especially when they are under threat from rivals, including open letters. Maybe we will appear in another piece of their social media soon!



 Ian Ferguson | VP Marketing
Ian Ferguson | VP Marketing



