I was lucky enough to be in Germany last week for Electronica, a massive show held every two years. This year, according to the organizers, around seventy thousand people attended the four-day event. This show is more focused on applications outside Lynx’s core focuses of military, aerospace, and federal, so we didn’t have a booth. However, it was great to see the industry coming back to meet in person.
I had the chance to present at four forums across the week and get a feeling for the big themes that were being discussed.
|
Image courtesy of Electronics Specifier
|
Nitin Dahad and Ian Ferguson
|
RISC-V
There is clearly significant uptick in interest in this processor architecture. We are hearing about it more in our core markets, with
announcements such as that from NASA and the
upstreaming of Android being pointed to as credible proof points of the system-on-chip (SoC) capabilities that the ecosystem is building around this open architecture. For every company that is publicly discussing RISC-V plans, there is at least three more that are working on the technology in a stealth mode. This is a technology that is very much part of our roadmap plans, especially with the somewhat imminent addition of hardware virtualization to SoC implementations.
CYBERSECURITY
The last few years have clearly shown a lot more progress in terms of adding hardware security capabilities to processors, particularly in the Arm ecosystem around the Cortex-M33 and ongoing broadening of companies that provide offerings compatible with the platform system architecture. I had the chance to talk with one of my favorite journalists, Nitin Dahad, about some recent examples of malware being introduced by containers. We went on to review some best practices around the use of containers and where we see unikernels, such as
LynxElement, fitting in as part of a strategy to reduce the attack surface.
ai/machine learning
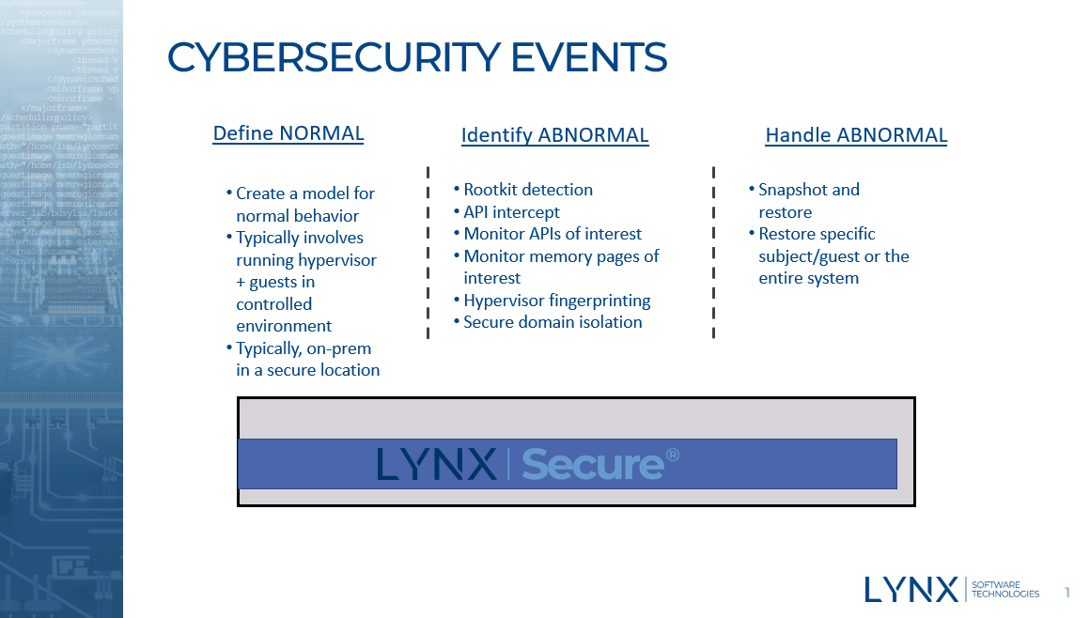
After a lot of hand waving about Artificial Intelligence and Machine Learning, this show seemed to showcase some tangible examples of how to embrace it and the benefits it is bringing to actual use cases. For us, one of the areas of focus is how the combination of hypervisor and applications can be used to give a much earlier detection of systems that have been compromised. This is important, as many times it can take hackers some time to identify valuable assets. There are many stories about systems being accessed and companies taking months to realize the incursion. One such example is shown
here. Hypervisors are placed in an ideal location in the stack to gather important system information which can then be used for system health. As I outlined in the line below, systems need to “define” normal, then “identify” abnormal and then “handle” (or recover from) abnormal. See image below.
Materials around these three areas are available from me. Just drop an email to me
here.



 Ian Ferguson | VP Marketing
Ian Ferguson | VP Marketing