C2 Server: What Is It? What Can Be Done to Thwart Them?
what is a c2 server Cybersecurity attacks are on the rise across a diverse set of markets. Behind the more intentional attacks is a desire to extract valuable information from a system or...

what is a c2 server Cybersecurity attacks are on the rise across a diverse set of markets. Behind the more intentional attacks is a desire to extract valuable information from a system or...

Overcoming Challenges, Embracing Innovation, and Redefining Business Models The concept of “digital transformation” is hardly new. Since the ‘90s, the phrase has become a widely used, some would say...

I am certain that there will be some formal write-ups in the coming days from esteemed journalist channels like Military Embedded, but we thought we would share some of what we heard out of the...
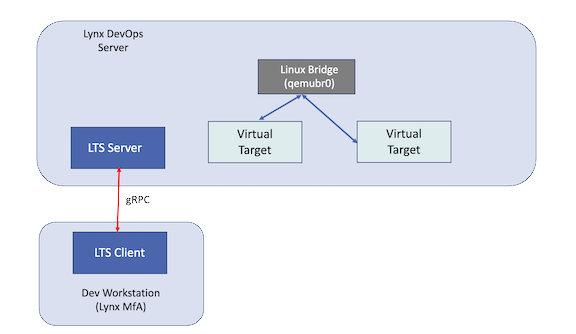
Report after report showcases the challenges that the Military and Aerospace market sectors face when delivering programs on time on budget and with the committed level of functionality.
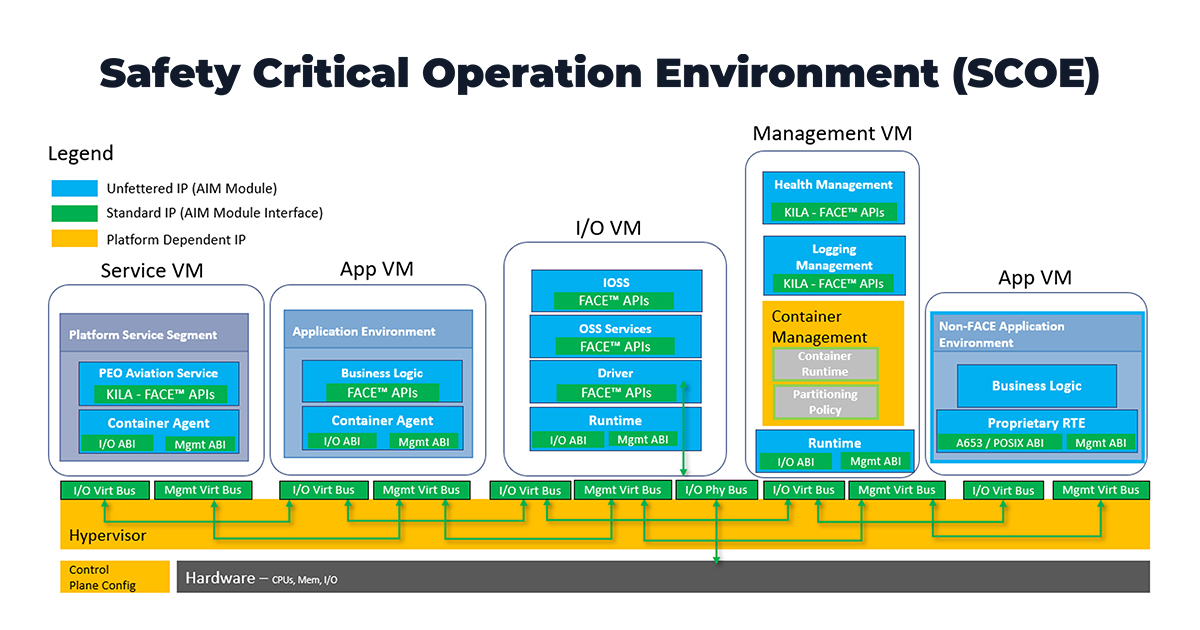
At Lynx, we see the support of standards for mission-critical systems as just the start. That is because APIs don’t define system behavior and timing. This thoughtful piece by our CTO, Will Keegan,...
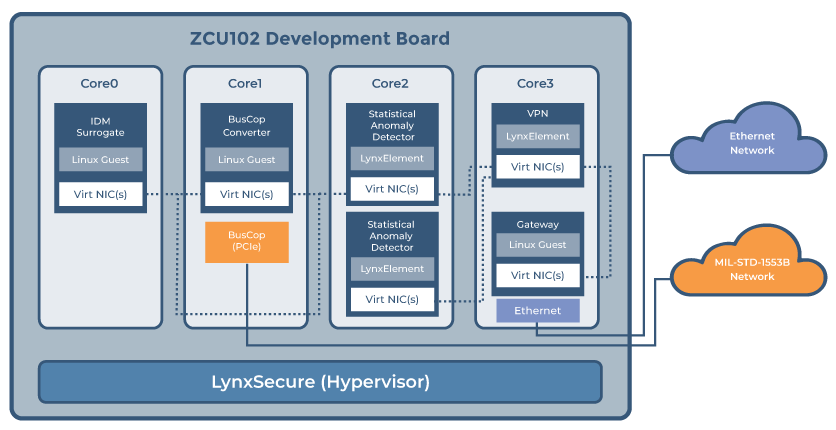
Followers of Lynx will know that our primary focus is LYNX MOSA.ic. This software framework, founded on the LynxSecure® separation kernel hypervisor, enables a variety of operating systems such as ...